Forget zero-days; the biggest cybercrime story of the last year is about keys, not code. For the first time, abusing valid accounts has dethroned phishing as the top infection vector, accounting for 30% of all incidents; a 71% surge. This isn’t about hackers breaking down the door; they’re using stolen keys from the thriving marketplace of dark web to simply walk in. Your identity is now a commodity and business is booming.
The dark web, a hidden internet layer accessible only via tools like Tor, is a study in contrasts. It’s a vital sanctuary for journalists and activists under repressive regimes, yet it has also morphed into a hyper-efficient bazaar for cybercrime. Here, stolen credentials can sell for less than a takeout meal and infostealer malware ads surged by 266% in 2023. For the tech-savvy, understanding this isn’t curiosity; it’s defense against the industrial-scale weaponization of everyday logins.
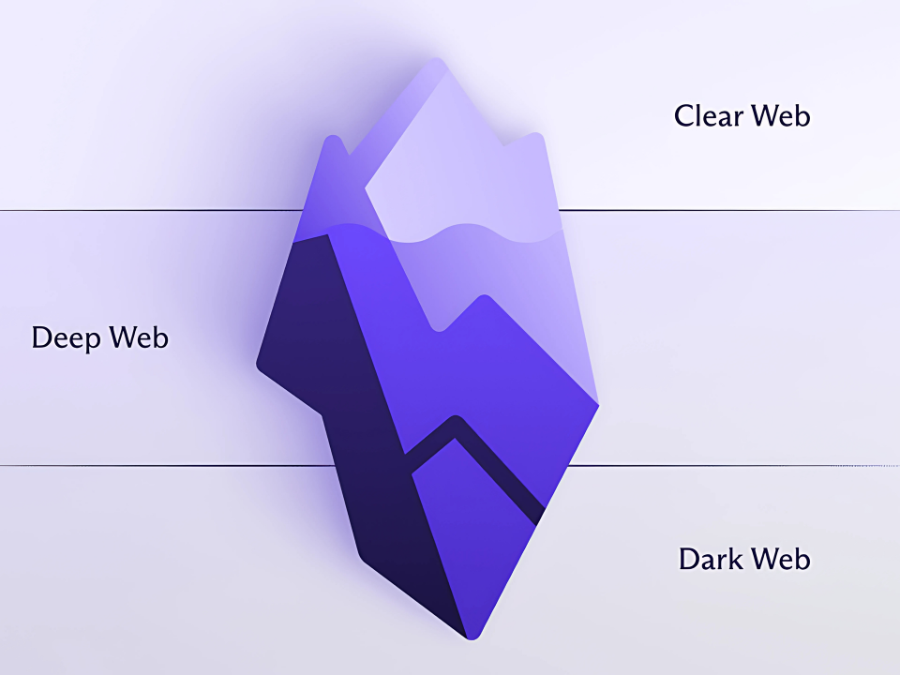
To grasp this digital iceberg, you need a guide who’s been there. This walkthrough explains the dark web’s layered architecture; and why your data might already be on the menu.
A Guide to the Dark Side of the Internet
The most significant shift is the commoditization of access. Attackers now prioritize stealing credentials because valid accounts offer silent, persistent entry without triggering alarms. This has created a brutal efficiency that fuels the entire cybercrime ecosystem.
| Feature | Traditional Tech | New Tech | Why You Care |
| Initial Access | Phishing emails | Infostealers (+266% YoY) | Faster, automated credential harvesting |
| Monetization | Ransomware encryption | Credential sales (+71% YoY) | Lower risk, higher ROI for attackers |
| Defense | Signature-based tools | Dark web monitoring | Find your leaked data before it’s used |
Comparing old and new security models is like comparing a moat to a motion-sensor network. Legacy defense focused on keeping attackers out but modern threats assume they’re already inside; the rise of “living-off-the-land” techniques using native OS tools makes malicious traffic look benign. This makes dark web intelligence non-negotiable; it’s the early-warning system that tells you the keys have been copied before the thief even reaches the vault.
Curiosity is a powerful motivator. If you explore, do it safely; this demo reveals the shocking metadata leaks a standard VPN fails to stop.
How to Access Dark Web Safely in 2025
While AI dominated headlines, X-Force confirms no AI-engineered cyberattacks have appeared in the wild yet. The current threat remains human-driven, which is concerning enough when 84% of phishing emails now deliver infostealers. The real AI danger will emerge once a single technology nears 50% market share creating a unified attack surface. Until then, the focus must be on identity hygiene: enforcing MFA everywhere and consolidating fragmented identity systems that create exploitable sprawl.
Wondering about timelines? AI-driven attacks become a real risk only when one platform dominates the market and yes your password may already be circulating; 1.2 million credential sets were up for sale in Q4 2024 alone.
This isn’t theoretical. Intelligence shifts companies from reactive to proactive. One airline avoided a PR disaster when analysts confirmed a supposed “massive customer data leak” was only stolen third-party travel information not their core systems. Verification like this turns fear into strategy helping security teams focus on real risks and ignore criminal bluffing which is more common than many realize.
10 Best Dark Web Websites to Explore with Tor
The dark web’s power shrinks when you stop mythologizing it and start monitoring it; the most effective defenders study criminal communications as diligently as attackers study their victims. The solution is not just stronger passwords rather rethinking identity as the primary perimeter. In this economy your greatest advantage isn’t a smarter AI but a healthy dose of paranoid optimism.
Want to Explore Urban Legends? : https://thecircuitdaily.com/the-red-room-myth-debunked/


Pingback: The Dark Web Demystified: Privacy, Myths, and Real Risks
Pingback: The Dark Web’s Red Room Myth: Scams, Hoaxes, and Truths
Pingback: Router Security Checklist: Lock Down Your Home Wi-Fi in Minute
Pingback: Home Network Troubleshooting: Checklist for Internet Issues
Pingback: First-Time NAS Setup with OpenMediaVault Explained - The Circuit Daily | Elite Tech Insights